Table of Contents
- Infrastructure and Security Overview
- Our Cloud Regions
- Our Availability Zones
- The Data Centers
- The PoPs and Network Resilience
- Our Strategic Security
- Disaster Recovery and Backup
- Uptime Over 99.9%
- Continuous Data Backup
- Network and System Security
- System Integrity Protection
- Application Security
- Capacity / Load Testing
- User Authentication
- Data Sharing and Role-Based Access Control
- Data Encryption
- Mobile Applications
- Account and Content Recovery
- People
- Privacy
- Enterprise-Grade Security
Our Global Infrastructure and Security Strategy
Infrastructure and Security Overview
Last update: October 21st, 2025. Lime Street Inc.
Lime Street is a cutting-edge digital placement and work management platform, helping insurers, brokers and organizations around the world align insurance placement with the most important objectives, efficiencies, and supporting tools. That help streamline the process while maximizing the ability to drive results.
We are dedicated to making Lime Street the most secure and reliable placement and management platform on the market. We are committed to protecting, commercial, personal and any form of data we receive, secure and redundant within our platform, which is why we continue to invest in the security of our services to not only meet, but exceed industry standards.
Security has always been a major topic of priority for Lime Street with the founders coming from a long career in Information Technology and Internet Security. Having played in this arena for many years the CEO and C Suite have expressed this as a number one priority year over year. We have tirelessly reviewed and adapted our approach around building a robust and mature security strategy since the day the company was conceived in 2015. Below is an overview of Lime Street’s security strategy, which includes an in-depth approach across our six key areas: Cloud Infrastructure, Security /Recovery, Networking, Systems, Application, and People.
Lime Street hosts its mission-critical Infrastructure and services within Amazon web services redundant and scalable hosting environments across the world. This decision was made at the very beginning of our journey and has stood us in great stead ever since. Partnering with AWS and other hosting providers has significantly more advantages around security, service’s and more features within those services, than any model, spanning from infrastructure technologies like compute, storage, and databases–to emerging technologies, such as machine learning and artificial intelligence, data lakes and analytics, and Internet of Things. This makes it faster, easier, and more cost effective to manage our existing applications and build nearly anything we can imagine. Our Services run within data centers located in the US, UK, EU and Asia and our Global infrastructure has been designed and built to deliver the most flexible, reliable, scalable, and secure cloud computing environment possible with the highest quality global network and performance available. From the PoPs, Network, DC’s all the way to Availability Zones and Region across the globe.
Using AWS has given us the most extensive global cloud infrastructure possible, while providing Regions with multiple Availability Zones connected by low latency, high throughput, and highly redundant networking. We have over 77 Availability Zones within 24 geographic regions around the world, and AWS has announced plans for 18 more Availability Zones and 6 more AWS Regions in Australia, India, Indonesia, Japan, Spain, and Switzerland. The AWS Region/Availability Zone model has been recognized by Gartner as the recommended approach for running enterprise applications that require high availability.
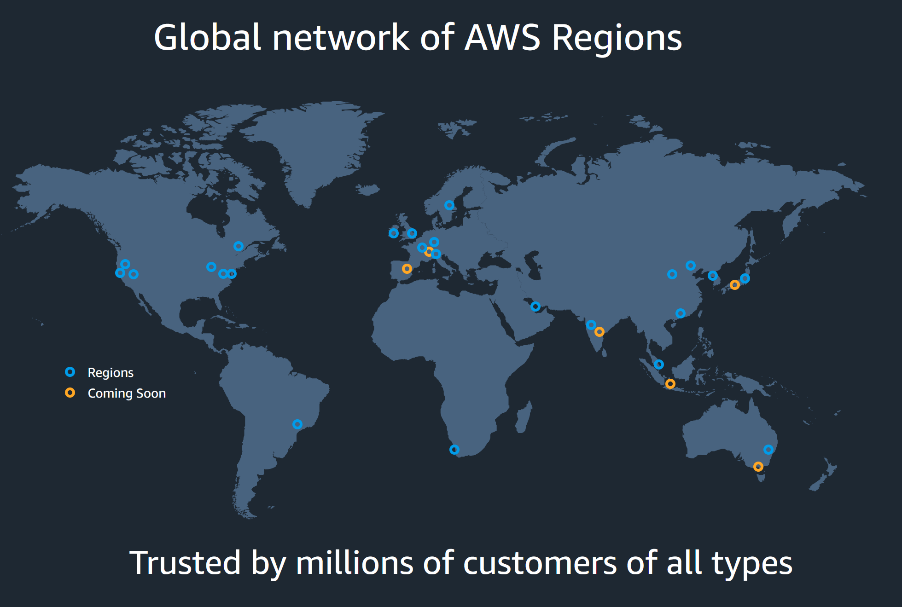
Our Cloud Regions
Each AWS region provides full redundancy and connectivity to the network. Unlike many cloud providers who define a region as a simple data center. Our model allows for Regions to consist of multiple availability zones, each of which is a fully isolated partition of the AWS infrastructure that consists of discrete data centers, each housed in separate facilities. Regions are connected to the global network with a 100GBPS intercontinental network. We also run DR zones within our Secondary and Tertiary tier 1cloud provider network from the likes of Google and Rack Space. This is completed redundant and outside of our primary environment.
- Lime Street's Primary, Secondary and Tertiary US location are based within Virginia (6 availability zones), Oregon (4 availability zones) and Ohio (3 Availability zones) and all fall within our governance and management policy forming a structured in-house resilience plan for Primary, Backup and DR best practices. The Regions and Availability zones are fully ISO 27001, SOC1, and SOC2 compliant. The facilities are Geographically redundant and located in Virginia, Oregon and Ohio along with other territories across the globe. With Multiple Secondary and Tertiary Regions and Availability zones.
- Lime Street's Primary UK location are based within AWS UK, and have 3 availability zones and is compliant with ISO 27001 as well as ISAE 3402 standards (an equivalent to SSAE 16). This data centers are specifically isolated for UK customers and their data.
- Lime Street's Primary European locations are based within AWS Paris, and have 3 availability zones and is compliant with ISO 27001 as well as ISAE 3402 standards (an equivalent to SSAE 16). This data centers are specifically isolated for EU customers and their data.
- Lime Street's Primary APAC locations are based in AWS Singapore, and have 3 availability zones and are compliant with ISO 27001 as well SOC 1,2,3 or as ISAE 3402 standards (an equivalent to SSAE 16). These data centers are specifically isolated for APAC customers and their data.
Our Availability Zones
These zones provide us with the ability to operate production applications and databases that are more highly available, fault tolerant and scalable than would be possible from a single DC. Each availability zone is a fully isolated partition of the global infrastructure. This means that it is physically separate from all other availability zones – not just two racks at opposite ends of a data center hall with a firewall between! Fully redundant and ready to fail over as expected.
Regions are composed of multiple Availability Zones that are designed to be independent of each other. Each Availability Zone is separated by a meaningful physical distance from other zones to avoid correlated failure scenarios due to environmental hazards like fires, floods, and tornadoes. Each Availability Zone also has independent physical infrastructure: dedicated connections to utility power, standalone backup power sources, independent mechanical services, and independent network connectivity within and beyond the Availability Zone. This design limits faults in any of these systems to just the one affected AZ. Despite being geographically separated, Availability Zones are located in the same regional area which enables high-throughput, low-latency networking. The entire AWS region (across all Availability Zones, consisting of multiple physically independent data centers) can be treated as a single logical deployment target for your workload, including the ability to synchronously replicate data (for example, between databases). This allows you to use Availability Zones in an active/active or active/standby configuration.
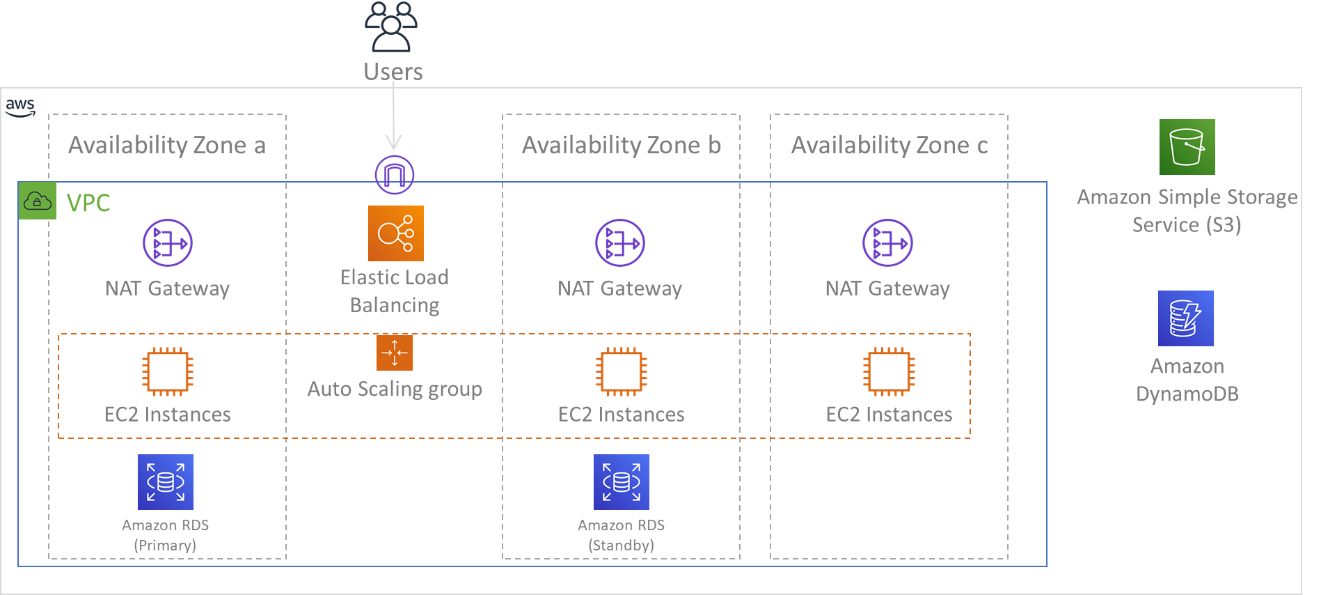
The Data Centers
The Data Centers themselves are cutting edge in design and security, securely built protected from manmade or natural risks. To ensure maximum reliability each are designed to redundancy within the 4 critical services needed; Redundant Power, Dedicated Fiber, Connectivity, and location security. This includes gated and guarded facilities with 24/7/365 year-round external monitoring and protection. These facilities also conform to industry controls and automated systems and undergo third party audits to confirm Security and Compliance of the highest level.
The PoPs and Network Resilience
With Amazon CloudFront, AWS operates the largest global content delivery network (CDN) of any cloud services provider in the world. Allowing us to securely deliver low latency and high transfer speeds worldwide. The CDN has over 216+ Points of Presence and consists of edge locations and regional Cache servers across the globe, with ever-expanding edge territories coming onboard.
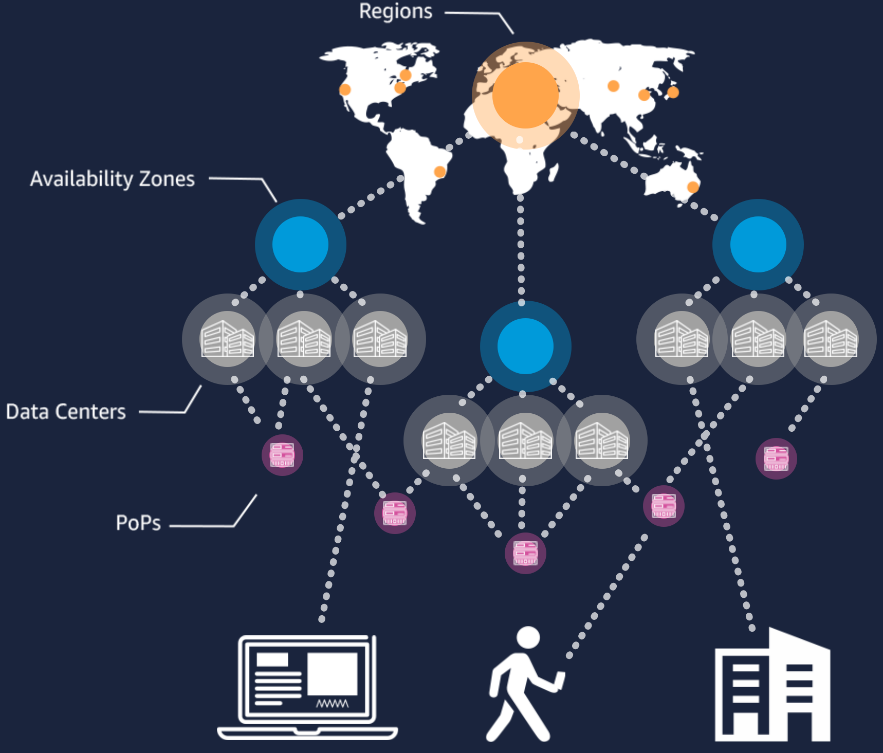
These facilities feature 24/7 manned security, fully redundant power backup systems, physical access controls, biometric authentication systems, extensive seismic bracing, the latest in early-detection smoke and fire alarms, and digital surveillance systems. All server and network components are continuously monitored by internal Lime Street staff and by the colocation providers.
Our Strategic Security
Our security is deeply important to us from the Top of our organization to the bottom. It’s key that we had all stakeholders and all team members trained on Cyber awareness along with an internal strategy of continual education around Security and integrated within the design of our cloud architecture and supported by our AWS offerings. These practices have been designed to easily and efficiently build secure, high-performing, resilient, and efficient infrastructure for our applications. World-class security experts monitor our infrastructure and support us within AWS. Our in-house security strategy allows us to build services and solutions that have strategic focus and benefits critical to helping us maintain an optimal security posture:
Prevent
Define user permissions and identities, infrastructure protection, and data protection measures for a smooth and planned adoption strategy.
Detect
Gain visibility into our organization’s security posture with logging and monitoring services. Allowing us to Ingest this information into a scalable platform for event management, testing, and auditing.
Respond
Automated incident response and recovery to help shift the primary focus of security teams from response to analyzing the root cause.
Remediate
Leverage event-driven automation to quickly remediate and secure our environment in near real-time.
Other AWS services and features that can support our data classification include, but are not limited to:
- AWS Identity and Access Management (IAM) for managing user credentials, setting permissions, and authorizing access.
- AWS KMS or AWS CloudHSM for encryption key Management with AWS-generated keys or bring your own key (BYOK) with FIPS 140-2 validation.
- AWS CloudTrail for extensive logging to track who, what, and when data was created, accessed, copied/ moved, modified, and deleted.
- AWS Systems Manager to view and manage service operations like patching along with AWS Inspector to conduct vulnerability scans.
- AWS GuardDuty for intelligent threat detection supporting continuous monitoring requirements.
- AWS Config to manage configuration changes and implement governance rules.
- AWS Web Application Firewall (WAF) and AWS Shield to protect web applications from common attack vectors (e.g., SQL Injection, Cross-Site Scripting, and DDoS).
Disaster Recovery and Backup
Having backups and redundant workload components in place from the start was key to our DR strategy for the restoration of our workloads had to come first and had to be set based on business impacts and needs. We have a solid implementation strategy to meet these objectives, considering the locations and function of workload resources and data. The probability of disruption and cost of recovery are key factors that inform the business value of providing disaster recovery for workloads such as our Inspection Management Portal or our Arc Home ios and android application, all the way through to our flagship Digital Placement Platform solution.
Both Availability and Disaster Recovery rely on the same best practices such as monitoring for failures, deploying to multiple locations, and automatic failover. However, our Availability focuses on components of the individual workload, while our Disaster Recovery focuses on discrete copies of the entire workload and platform. Disaster Recovery has different objectives from Availability, focusing on time to recovery after a disaster.
Define recovery objectives for downtime and data loss: The workload has a recovery time objective (RTO) and recovery point objective (RPO).
Recovery Time Objective (RTO) is defined by the organization. RTO is the maximum acceptable delay between the interruption of service and restoration of service. This determines what is considered an acceptable time window when service is unavailable.
Recovery Point Objective (RPO) is defined by the organization. RPO is the maximum acceptable amount of time since the last data recovery point. This determines what is considered an acceptable loss of data between the last recovery point and the interruption of service.
Our recovery (DR) strategy has been defined to meet our workload objectives. Such as: backup and restore; standby (active/passive); or active/active, dependent on the application and customer landscape in question but we have the ability to do both with our redundant infrastructure and agile methodologies.
When architecting a multi-region disaster recovery strategy for our workloads, we choose all three of the following multi-region strategies. They are listed in increasing order of complexity, and decreasing order of RTO and RPO. DR Region refers to an AWS Region other than the one primary used for your workload (or any Tertiary Region if your workload is with multiple providers).
- Backup and restore (RPO in hours, RTO in 24 hours or less): Back up your data and applications using point-in-time backups into the DR Region. Restore this data when necessary to recover from a disaster.
- Pilot light (RPO in minutes, RTO in hours): Replicate your data from one region to another and provide a copy of your core workload infrastructure. Resources required to support data replication and back-ups such as databases and object storage are always on. Other elements such as application servers are loaded with application code and configurations but are switched off and are only used during testing or when Disaster Recovery failover is invoked.
- Warm standby (RPO in seconds, RTO in minutes): Maintain a scaled-down but fully functional version of your workload always running in the DR Region. Business-critical systems are fully duplicated and are always on, but with a scaled-down fleet. When the time comes for recovery, the system is scaled up quickly to handle the production load. The more scaled-up the Warm Standby is, the lower RTO and control plane reliance will be. When scaled up to full scale this is known as a Hot Standby.
We see the best disaster recovery implementation is when we validate the implementation regularly: We regularly test failover to DR to ensure that RTO and RPOs are met.
Uptime Over 99.9%
Over many years of service, Lime Street has consistently met or exceeded a 99.9% uptime, ensuring customers can access their tasks and projects when needed without interruption.
Continuous Data Backup
Lime Street’s data backup model provides near real-time database replication to ensure customer data is both backed up and available on redundant and geographically dispersed servers. Full backups, snapshots and redundant copies are performed and or sent to offsite locations on a daily basis and are stored at rest and in transit in an encrypted environment physically separated from the primary servers to ensure fault tolerance.
Network and System Security
Tenable Network Security Infrastructure
Lime Street uses industry-standard network protection procedures, including network segregation using the AWS network and a combination of AWS VPC, VLANs, load balancers, firewalls and router technologies, intrusion detection and prevention systems, centralized log systems, and alert mechanisms. These procedures are used together with secure connectivity, including secure channels and 2FA multi-factors for authorized systems, operations groups, personnel, and end-user access. This allows us to prevent, detect, and promptly remediate the impact of malicious traffic and network attacks.
Regular Updates and Patch Management
Regular interval-based internal network security audits and scanning gives us an overview for quick identification of any impacted systems and services. According to our in-house patch management policy, operating systems, software, frameworks, and libraries used in Lime Street infrastructure are updated to the latest versions on a regular basis by either the AWS service or by the in-house team. Whenever a vulnerability in a product used by Lime Street or a high or critical vulnerability is publicly reported, prompt actions are taken to mitigate any potential risks for our customers — we apply hotfixes and patches promptly when available and/or implement pro-active mechanisms like configuration of firewalls or IDS/IPS.
System Integrity Protection
Lime Street uses operating system-based and custom integrity check services to ensure the integrity of all critical files and system objects. A quick response to any potential unauthorized changes to the system helps ensure our customers are using Lime Street-approved application services.
Application Security
Application Security Process
An in-depth Application Security Lifecycle process is fully integrated into Lime Street’s Software Development Lifecycle (SDLC), including:
- Defined in-house security requirements, policies, and industry security best practices applied in every stage of the lifecycle.
- Ongoing security review of architectures, design features, and solutions.
- Iterative source code review for security weaknesses, vulnerabilities, and code quality, plus development team advisory and guidance.
- Regular assessment of our stage and pre-production environments.
- Security training conducted for IT teams according to their respective job roles.
- Due to the multi-tenant and multi-user-type nature of the system, we give special care to developing tests that ensure that our security model remains watertight. This involves testing endpoints for permission restrictions and that users can only make changes to objects that they own. This gives us confidence that the data is partitioned correctly, and that no information is leaked across boundaries.
Regular Penetration Testing
Lime Street conducts both automated and manual vulnerability / penetration testing against our systems.
Automated scanning is run monthly as well as on all new major releases, and manual penetration testing is conducted annually. Lime Street endeavours to evaluate and, where deemed necessary, correct any issues highlighted in these tests within 48 hours for serious issues, 7 days for medium-priority issues and 14 days for minor issues. Once issues have been corrected, the scan will be re-run to verify the fixes.
Capacity / Load Testing
Network / Application Servers
Our application servers and network are set up to auto scale based on load, with no practical upper bound to capacity. This is confirmed by regular simulations with high numbers of users.
Database
We have developed a tool that seeds the critical database tables with relatively large amounts of data. We see a critical table as one that will grow over time and therefore could become a victim of a missing index.
We created a simple model that we think reflects the system with respect to how many rows should be inserted into each table relative to one another. The model works by taking an initial value for the number of customers in the system and then using a multiplier that we feel is appropriate. We then use another multiplier to determine the number of data points for each customer and so on. This gives us a realistic worst-case scenario database size to test with.
User Authentication
Each user in Lime Street has a unique, password-protected account with a verified email address. The password is validated against password policies and stored securely using a strong hashing algorithm with a unique salt for every password. 2-Factor Authentication is available as an additional security measure to protect Lime Street accounts. Lime Street could also support multiple methods of federated authentication, including but not exclusively, Google Open ID, Azure, Office 365, ADFS, and SAML2 to conveniently and securely gain access to a Lime Street account leveraging corporate credentials. Lime Street also offers advanced security settings that allow customers to manage Network Access Policy and Password Policy. More details can be found in our user manual.
Data Sharing and Role-Based Access Control
A Lime Street account administrator manages and controls individual user rights by granting specific types of user account at setup and onboarding of new users. Details about various user accounts, roles, and authorization controls in Lime Street can be found in our user manual.
Customer data can only be accessed by authorized users within their Lime Street account.
Lime Street offers flexible data access control setup by allowing admins to configure Customized Access Roles, which offer a choice of different permissions for user actions in Lime Street and can be used to specify user or group access levels to certain areas of the platform. Selective sharing can be enabled to give greater access control over specific documents or datasets. Lime Street allow administrators to holistically review user access to sensitive data.
Data Encryption
Lime Street uses Transport Layer Security (TLS) 1.2 with a preferred AES 256 bit algorithm in CBC mode and 2048-bit server key length with industry-leading modern browsers. When you access Lime Street via web browser, mobile applications, email add-in, or browser extension, TLS technology protects your information using both server authentication and data encryption. This is equivalent to network security methods used in banking and leading e-commerce sites.
All users’ passwords, cookies, and sensitive information are reliably protected from eavesdropping. User passwords are hashed with industry-standard algorithms, and user files uploaded to Lime Street servers via both web application and API are automatically encrypted with AES 256 using per-file keys. If someone were to gain physical access to the file storage, this data would be encrypted and impossible to read directly. These encryption keys are stored in a secure key vault, which is a separate database decoupled from the file storage layer. In addition, all Lime Street workstations and servers are encrypted at rest using file system encryption where AES 256-bit is used.
Mobile Applications
Your Lime Street workspace is accessible via Android and iOS applications, which inherit security functionality from Lime Street’s web-based application. These applications also have additional security features like encryption at rest based on the native security of the user’s device.
Account and Content Recovery
You can also safely recover accidentally deleted items from Lime Street by contacting support. If an item or event is deleted by mistake, there is a possibility to recover the deletion event if you contact us within 2 business days. Some user account information can be recovered for up to 7 days after deletion.
People
Processes
Designing and running Cloud infrastructure requires not only technology, but also a disciplined approach to processes, Governance and good Management Policies. This includes policies about escalation, management, knowledge sharing, risk management, and day-to-day operations. Lime Street’s security and operations teams have years of experience designing and operating cloud hosting and Its security services, and we continually improve our processes as time moves on. Lime Street has also developed best-in-breed practices for managing security and data protection risk. All of these elements are essential parts of Lime Street’s security culture.
Need-to-Know and Least Privilege
Only a limited set of employees have access to our cloud infrastructure or codebase along with the data stored in our databases and systems files. There are strict security policies for employee access, all security events are logged and monitored, and our authentication methods and data are strictly complied to.
We limit access to customer data to employees with a job-related need, and require all these staff members to sign a confidentiality agreement and maintain a level of continued learning around our internal and external systems along with an awareness cycle every 6 months for cyber awareness and information security.
Privacy
GDPR & CCPA: For customers who request it, we have a Data Processing Addendum and CCPA Addendum that outlines the obligations Lime Street has in its role as a provider of the Lime Street Service to Customer. This may include obligations related to the General Data Protection Regulation (Regulation (EU) 2016/679) (GDPR), Standard Contractual Clauses (SCCs), and California Consumer Privacy Act (CCPA) as well as other applicable laws.
The Lime Street Privacy Policy has been carefully cultivated to address your privacy concerns and your rights with regards to your personal data. If requested, Lime Street will also provide a Data Protection Addendum, which describes our data practice.
Infrastructure and 3rd party Compliance certificates

SOC2 Type II: This independent, third-party examination assesses the nature and effectiveness of the internal controls Lime Street or Lime Street 3rd party vendors or services provider uses to protect customer data. SOC 2 Type II audits demonstrate Lime Street or their partner of choice’s commitment to taking a mature, robust, and secure approach to products, processes, and security as it relates to customer data.
ISO/IEC 27001:2013: This independent, third-party certification ensures Lime Street or Lime Street’s 3rd party vendors or services infrastructure use or has in place for an end-to-end security framework and a risk-based approach to managing information security. The certification illustrates Lime Street’s or their partner of choices dedication to a best practice security strategy aligned with international security standards.
ISO/IEC 27018:2019: This certification ensures Lime Street or Lime Street’s, 3rd party vendors or services infrastructure has measures to protect Personally Identifiable Information (PII) in accordance with the privacy principles in ISO/IEC 29100 for the public cloud computing environment. This demonstrates Lime Street or their partner of choice’s commitment to taking a mature, robust, and secure approach to products, processes, Data and security as it relates to customer data.
Enterprise-Grade Security
If you have any security questions and concerns, please contact our Sales Office at +1-305-400-4816
Or any additional questions or queries relating to this page please contact support@limestreet.io
Terms and Conditions
Please see our Terms and Conditions

Copyright © 2021-26 Lime Street Inc.
25 SW 9th St, 4th Floor,
Miami, FL
33130
